Microsoft implemented new functionality in Windows Defender Antivirus for Windows 10 recently that makes the antivirus solution run in a sandbox on the system.
The feature, which is available in Windows 10 version 1703 and newer, needs to be enabled for the time being as it is not active by default currently.
Microsoft hopes that Windows Defender Antivirus' new restrictive process execution environment helps protect the application against attacks that are targeted directly at it. Antivirus solutions often need to run with high privileges to protect the entire system against malicious attacks; the need to run with high privileges make antivirus programs high profile targets, especially if they are used widely.
Microsoft stated that it is unaware of targeted attacks "in-the-wild" against Windows Defender Antivirus but that security researchers identified ways to attack Windows Defender Antivirus successfully in the past.
A sandboxed environment adds another layer of protection to the antivirus solution. Malware that aims to exploit Windows Defender Antivirus successfully would have to exploit a vulnerability in the application itself and find a way to break out of the sandboxed environment that Microsoft created for the security software.
Running Windows Defender Antivirus in a sandbox ensures that in the unlikely event of a compromise, malicious actions are limited to the isolated environment, protecting the rest of the system from harm.
Enable Windows Defender Antivirus sandboxing
Sandboxing is not enabled by default at the time of writing. It is available, however, on all devices running Windows 10 version 1703 or higher.
Tip: if you are unsure about the Windows version run winver.exe on Start to display it.
Here is what you need to do to enable Windows Defender Antivirus sandboxing right now:
- Open the Start menu.
- Type powershell.exe to display PowerShell as one of the results.
- Right-click on the result and select "run as administrator" or hold down the Shift-key and the Ctrl-key before you select the result. Both options execute PowerShell with elevated rights.
- Confirm the UAC prompt that may be displayed.
- Run setx /M MP_FORCE_USE_SANDBOX 1.
- Restart Windows.
The command sets a new system variable that tells Windows to run Windows Defender Antivirus with sandbox functionality.
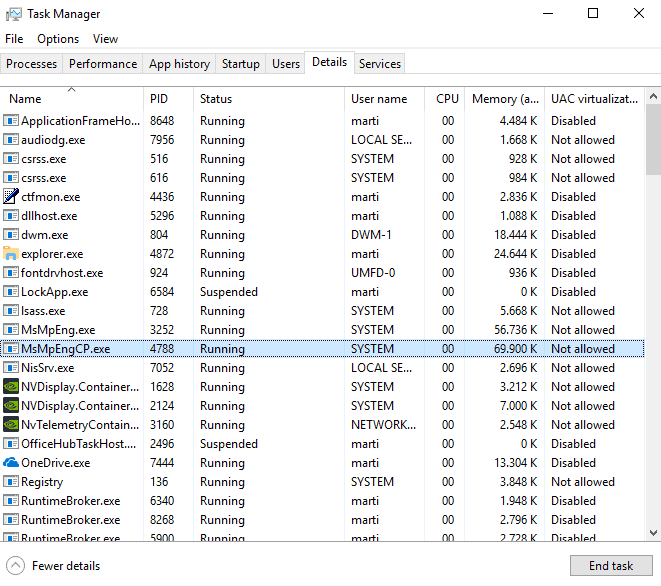
Verifying that the sandbox is running is simple: open the Windows Task Manager with a tap on Ctrl-Shift-Esc and make sure you display all details (click on more details if not), and look on the Details tab of the program.
Locate MsMpEngCP.exe there. If you see it, the sandbox is up and running. The process runs with low privileges and uses "all available mitigation policies" according to Microsoft.
You can use third-party programs like Process Explorer as well if you prefer those to verify that the sandbox is enabled.
Check out Microsoft's blog post on the Microsoft Secure blog for implementation details and challenges that Microsoft faced during research and development.
Now You: Which antivirus solution do you run?
Ghacks needs you. You can find out how to support us here or support the site directly by becoming a Patreon. Thank you for being a Ghacks reader. The post The Windows Defender Antivirus Sandbox in Windows 10 appeared first on gHacks Technology News.

Comments
Post a Comment